*Book Review, Penetration Testing with BackBox: Stefan Umit Uygur (Author)
Since I read a book about Kali Linux recently, I wonder is there any other penetration testing tools exist like Kali. I came across with a BackBox, which is based on Ubuntu and has black& white-hat hackers features. Like a Kali linux, Backbox also comes with lots of security tools like web application analysis and stress test etc with a light desktop manager named XFCE. Since BackBox designed to use very low memory and resources to function with pretty old and obsolete hardware for normal audition platform. Unlike the book that i recently read about Kali linux, this book doesn’t describe how to download and setup environment for vmware or other way, so I had to search and installed it by myself. (maybe it’s pretty easy to install ios to vmware)
Chapter 1 : Starting Out with BackBox Linux
This chapter is summary of security features and tools installed on a Backbox starting with Information Gathering tools, Vulnerability Assessment and Miscellaneous tools. Most of feature seems pretty similar with Kali linux tools, but I find in a Backbox, there’s documentation & reporting tools and reverse engineering tools. Also it’s pretty cool that there’s anonymous on the main menu, which helps the user invisible to the network.
Chapter 2 : Information Gathering
On Chinese The Art of War, there’s term ‘知彼知己 百戰不殆’, which has similar meaning with ‘Know your enemy and who you are then you will never lose’. Information gathering is very basic step yet very important step of ethical hacking / security assessment. Collecting lot of information about a target is useful to plan the assessment further.
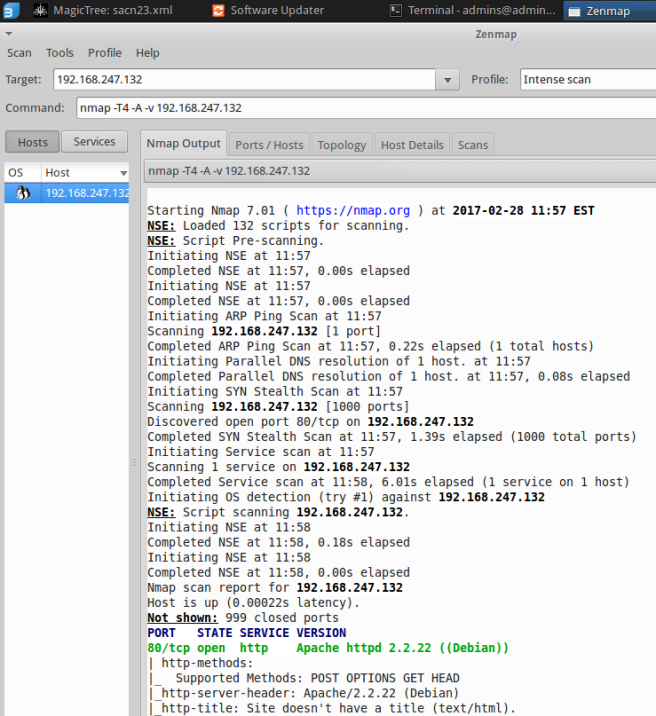
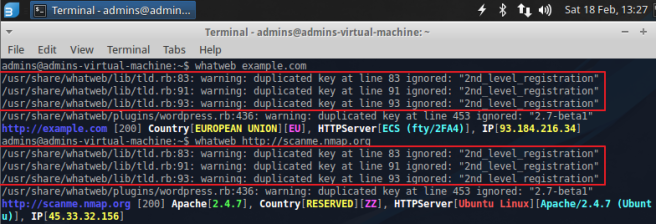
Whatweb is an effective tool to figure out what kind of apps for target side. You can find hatweb menu on [Auditing] > [Information Gathering] > [Web Application], and easy to use just type ‘whatweb target web address’. I find there’s warning message with “duplicated key with 2nd_level_registration”, which caused by ruby issue. But you can still see the target’s IP address and other information after three warning messages.
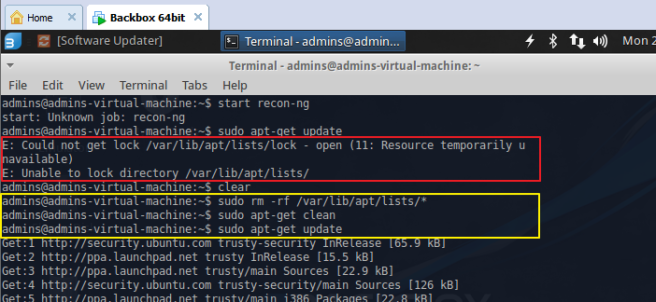
*If you have any trouble with finding tools on menu, you might want to check whether your backbox has that tools or not. If there’s no command related to the program then you might want to install it, for example, type ‘sudo apt-get recon-ng’ (it might ask you type a password), if it shows with E: Unable to lock directory or E: Could not get lock / errors, then you need to type
‘sudo -rm -rf /var/lib/apt/lists/* ‘
‘sudo apt-get clean’
‘sudo apt-get update’ or ‘sudo apt-get whatweb’
For more details, https://www.maketecheasier.com/fix-ubuntu-update-errors/
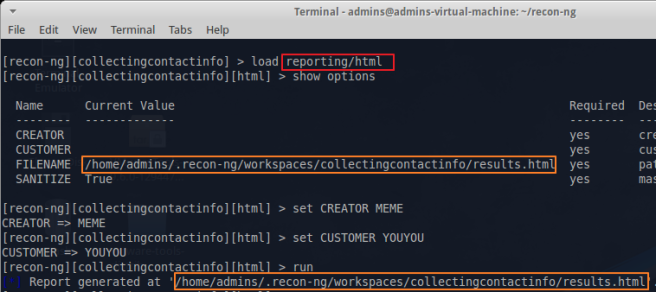
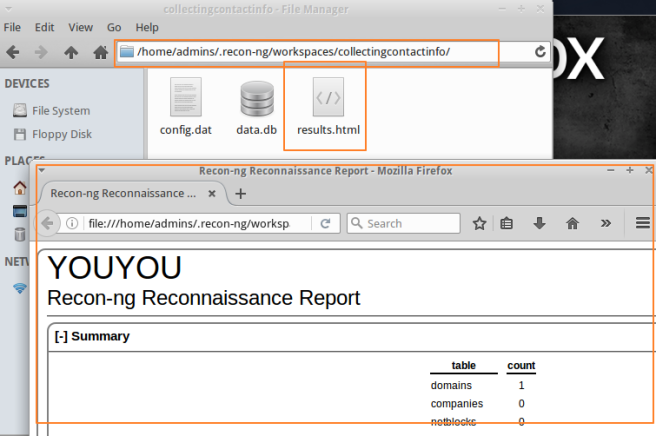
Recon-ng is well-known tool for information gathering, like the book described, one of its relevant feature is modularity, which means you can download the useful module or build your own to narrow it down the information. To install recon-ng on backbox, you need to type ‘git clone https://LaNMaSteR53@bitbucket.org/LaNMaSteR53/recon-ng.git’ For more information, https://bitbucket.org/LaNMaSteR53/recon-ng/wiki/Usage%20Guide
*FYI :Since I download the recon-ng module somewhere else, I type ‘cd ~/recon-ng’ to find a recon-ng and type ‘./recon-ng’ command to start, you can also type a workspace name, if you want to make separate workspace ‘./recon-ng -w workspacename’. If you just type without workspace it will be assigned to a [default] workspace.
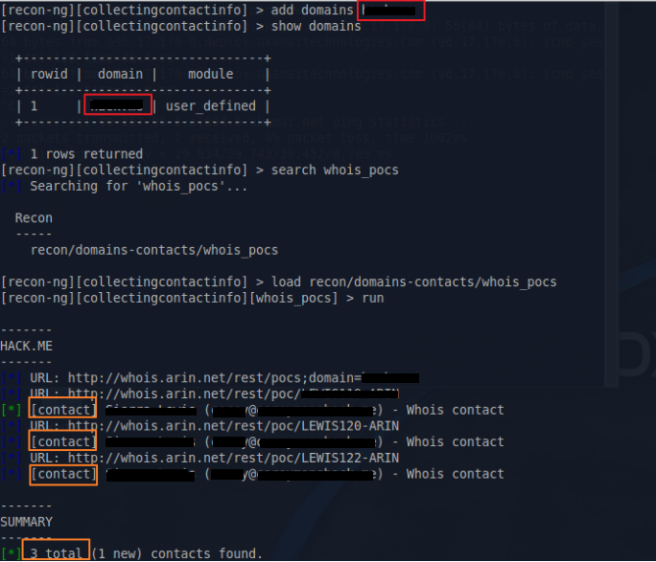
There’s 4 modules on Recon-ng, ‘Discover’, ‘ Experimental’, ‘ Recon’ and ‘Reporting’. There’s first example with ‘recon/hosts/gather/http/web/google_site’ module ,that i couldn’t find on updated version of recon-ng. Also another module, described on the book as ‘recon/contacts/gather/http/api/whois_pocs’ is now ‘recon/domains-contacts/whois_pocs’ (I use search key to find ‘whois_pocs’ module). Without searching a module on google, you can easily guess what this module does by checking out module’s name. This module collects domain-contacts like e-mail with whois method. So you have to load the module and set the domain by ‘add domains target.com’ and run.
Nmap
Nmap is also a well-known tool for information gathering, I’ve already learn few function on Kali linux book, but nmap is quite useful if you know the command with a port number and service. You can also get details of the application installed or running on the target machine , which means you can detect vulnerabilities from nmap.